Last week, computers around Europe have been a target of a massive email spam campaign containing malicious Javascript, which drops Locky ransomware (analysis by Malwarebytes).
ESET Antivirus as reported on the spike in detections (JS/Danger.ScriptAttachment) of a malware loader that uses Javascript. The campaign started on May 22 and peaked on May 25.

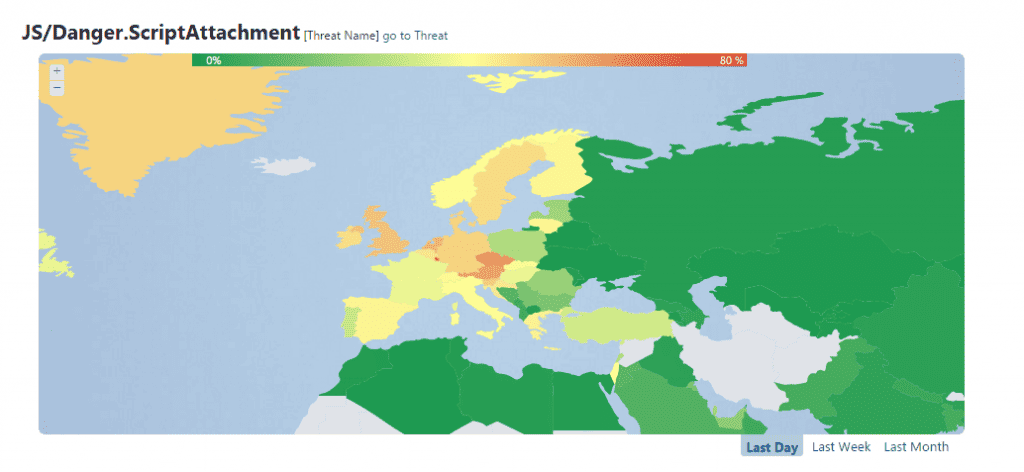
Countries all throughout Europe have been involved, with the top detection rates being seen in Luxembourg, the Czech Republic, Austria, the Netherlands and the U.K. The antivirus companies telemetry info also revealed major detection rates for this threat in Canada and the United States.
Country Statistics:
- Luxembourg: 67%
- Austria: 57%
- Netherlands: 54%
- Germany: 48%
- Denmark: 48%
- Sweden: 46%
- Belgium: 45 %
- Spain: 42%
- Finland: 42%
- Norway: 40%
- France: 36%
- Portugal: 30%
- Poland: 26%
JS/Danger.ScriptAttachment has in the past downloaded a variety of malware, but lately it’s been utilized to mainly deliver Locky, a popular piece of ransomware.
Currently Locky’s encryption has yet to be broken, but Bitdefender has released a free tool that prevents the infection in the first place. The tool makes the computer look like it’s already infected by the malicious program, so the malware will skip its installation.