In the 3rd issue of the recently released, Threat Horizons, Google’s Cybersecurity Action Team (GCAT) provides organizations with information about emerging risks and actionable mitigation.
Bad actors have always looked for loopholes such as misconfigured cloud resources for the primary objective of crypto mining and ransomware. The latest report focused on common attack vectors and countermeasures against the threats.
Most common attack vectors
Attackers continually focus attention on exploiting vulnerable cloud servers and weak passwords. In recent years, bad actors are leveraging the progressive increase in automation and computing power used by organizations to infiltrate cloud admin accounts and privileged users with brute-force attacks in a grand manner. The Google Cloud report shows brute force attacks targeting cloud services are the most common compromises in the first quarter of 2022.
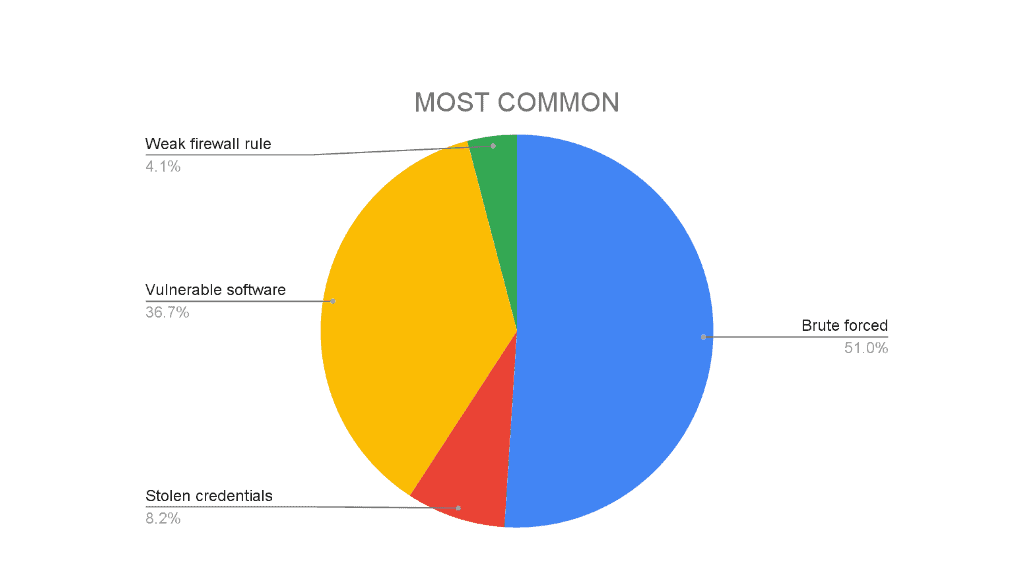
Trailing behind brute-forcing is software vulnerabilities. Many organizations operate with unpatched and outdated systems, which provide an easy entry for cybercriminals. One such leveraged by hackers to target the corporate network is the Log4j zero-day vulnerability, a flaw putting many open-source software applications at risk. As reported by Google’s project zero, there has been an uptick in zero-day vulnerabilities detected in 2021. Despite the unprecedented detections recorded in 2021, limited exploitation was reported by vendors before patching vulnerabilities.
Third on the list of the most common vector attacks in crypto mining and ransomware is compromised credentials leaked from public repositories. Multiple employers with shared credentials and other human errors increase the chance of compromise.
The last attack vector in the report is weak firewalls. Though it plays a less significant role in overall compromises, the likelihood of brute force and other attacks increases considerably with a weak barrier.
Hackers shifting focus from Files to databases
In the past, ransomware threat actors have mainly targeted computer file systems with the aim of data hostage and extorting organizations. This recent issue of Threat Horizons noted a switch of targets away from file to a more critical extorting model – databases.
The attackers’ tactics aim to brute force SQL servers and gain administrative access to encrypt sensitive information for ransom sent to a crypto wallet with a threat to delete the data. Another technique is duplicating a table or replacing the original table to hijack a cloud project. These security breaches are common in proof of concept (POC) instances, where weaknesses in non-working environments are exploited before being patched.
How Google Cloud users mitigate the security risks
After assessing the ransomware risks, the report further recommended these counteracting practices employed by Google Cloud customers.
- GCP’s security command center is handy for evaluating your cloud resources’ overall security health/risks. Defining Org policies also gives you fine-grained, centralized control.
- Google Cloud customers employ an additional defense layer with the Virtual Machine Threat Detection (VMTD) accessible in the Security Command Center against the exploits of crypto mining and ransomware groups.
- Detecting any authorized storage of secrets like credentials, tokens, and other sensitive information helps minimize compromise and infiltration.
- Lastly, setting up a container and web security scanner available in the Security Command Center to find outdated libraries, improper configuration, and other vulnerabilities greatly minimizes potential entry points.