Today, the dynamic moving image, GIF sent to a friend or colleague, perfectly expresses our emotions and lightens the mood of the receiver(s). However, several concerns have been raised about the leak of user information when searching and sharing the perfect GIF in some messaging apps. One of such was reported at Security Risk Advisors (SRA), where a researcher investigated Giphy’s integration on some popular messaging apps and detailed the findings along with suggestions for improving user privacy.
How Giphy may be tracking you
To integrate and open up the library that contains millions of GIFs and stickers for users, a request needs to be made from the search API on the client side. Every call returned a URL with the “cid” parameter and a 40-character search id. This search ID is determined by factors like search string, results requested, results rating, results offset, geographical area, and time of the search.
- When you make a search request, every GIF returned will have the same cid
- The first 8 characters (“app id”) are consistent across every search made with the same API token. For example:
- Teams searches start with “de9bf95e”
- Discord searches start with “73b8f7b1”
- Signal (on Android) searches start with “c95d8580”
Below is an example:
https://media0.Giphy.com/media/Ju7l5y9osyymQ/Giphy.gif?cid=de9bf95evmdivzh16orm7svyp9ticugu4abuyc3ty2df5y9i&rid=Giphy.GIF
Searches made from the same API key have the same first 8 characters. From the example above, de9bf95e is the app id for gif search on Team. Gif searches on Discord and Signal (Android) have app IDs of “73b8f7b1” and “c95d8580” respectively.
Also, the same search id is attributed to every image received from the same keyword search. Though it may change occasionally, the search id is consistent for subsequent searches with the same API key on the same host. That implies different people in the same geographical location get the same search id if the query is done on the same API key.
Given that the cid parameter is not dynamic, a gif URL sent to a friend leaves some footprints, though not your IP, in the message history.
Signal
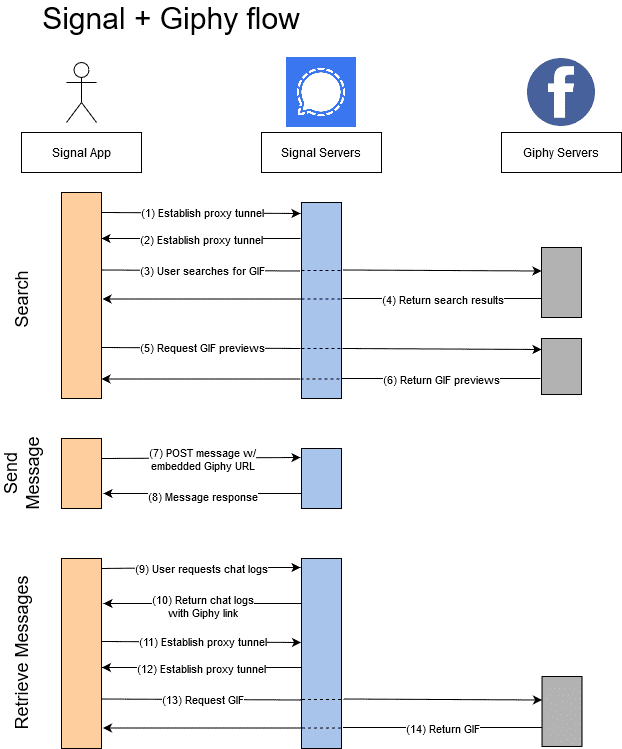
As explicitly stated in Signal’s blog posts here and here, Signal serves as a privacy-preserving proxy between the users and Giphy. It ensures there’s no direct communication between you, the Signal user, and the Giphy server. Your gif search on Signal is transferred over its assigned network API to Giphy. The way Signal communicates, no other data besides the cid parameter in the URL gets to Giphy’s servers.
In addition to that, the communication between Signal and Giphy is TLS, meaning both the plaintext sent and the result of your search are encrypted. In essence, Signal service knows who you are based on your data with them but not your search. The Giphy server, on the other hand, knows what you are searching for but not your personal information.
How Signal can improve privacy
Hard to improve the privacy on Signal without compromising the user experience. The encrypted, proxy setup makes it almost impossible for Giphy to know your IP address. However, it may employ small details like search patterns or cache to discern that the request is coming from the same host without knowing the origin. On the Signal side, there is a possibility of inflating user activity with fake searches and download requests. But the cost of bandwidth will make this tactic not worth Signal’s time.
Discord
Though Discord is powered by the Google GIF search engine, Tenor, users can search and send GIFs with Giphy using the /Giphy command. Unlike making a query on Signal, searching for GIFs this way creates a direct connection between the user and Giphy servers.

First, the discord app forwards the user’s search string to Giphy. A search result is returned to the discord server, which then processes the feedback and sends the preview URL to the user. From there, there is a direct line of communication with which the user requests previews directly from the Giphy servers. These preview requests contain the cid parameter and a referer header that leak user data to Giphy. Access to the exact URL channel from the referer header and other information in the cid parameter gives Giphy the foundation for constructing information about which channel you use, who you are messaging, your current emotional state, and so on.
It should be noted that this hypothetical scenario is different when sending and retrieving gifs where the requests are handled on a proxy.
In what ways can Discord improve your privacy?
The first is to remove the cid parameters from the preview URL before a request is sent to the Giphy servers. Also, not sending the referer header along with GIF preview requests eliminates a major privacy concern. Lastly, all proxy GIF previews should first be filtered through discord servers.
Microsoft Teams
For whatever reason, Microsoft grants Giphy a free hand when it comes to users’ privacy. If enabled by the admin, Request GIF previews from queries you make are sent directly to Giphy servers without proxy. With your cid token easily accessible on Giphy servers, the IP addresses of people in your group downloading your sent GIFs are available on a platter. Combined with other data collection techniques, It’s safe to say Facebook has what it needs to construct profiles of your colleagues, friends, and family as well as your emotions. Strangely, this privacy concern does not surface when you make use of a third-party custom search extension available on Teams. All media URLs are then converted to proxies URLs.

Final Thoughts
GIFs spice up our messaging and many people generally like them. However, some messaging apps may leak information as a result of poor design and negligence of user privacy. Signal seems more privacy-oriented without compromising user experience. On the other hand, Discord leaks a lot of information via GIF previews while Microsoft Teams apparently gives Giphy access to its user’s information.







