Security researcher, z0ccc, has released a new tool that proves that Google Chrome extensions can be fingerprinted which allows tracking of its users online.
Tracking users online is typically done via fingerprints that generate unique hashes for each user. These hashes are generated by combining installed Windows applications, the device’s screen resolution, GPU performance, hardware config, and installed fonts.
With these characteristics, sites will track your device across social media and various websites. Google knows who you are, your social media profiles and what sites you browse allowing them to tailor advertisements to what you interact with and habits.
Chrome exposing extensions to fingerprinting
z0ccc has released a site called ‘Extension Fingerprints’ along with the new tool which can generate an almost unique fingerprint based on your installed Google Chrome extensions. The full source of this tool is located on z0ccc’s GitHub page.
Chrome extension developers have the ability to declare specific assets within Chrome extensions as ‘web-accessible resources‘. This allows outside web pages or other extensions to access the plugin/extension itself.
These resources are normally an image file that is declared by utilizing the ‘web_accessible_resources‘ property that is located in an extension’s manifest file.
Here’s an example of a web-accessible resource:
"web_accessible_resources": [
{
"resources": [ "logo.png" ],
"matches": [ "https://zerosecurity.org/*" ]
}
],Originally disclosed in 2019 by Authentic8, it is possible to capture these web-accessible sources to find installed extensions and generate fingerprints of various browsers based on the combined uniqueness of browser extensions.
It is possible for extension authors to hide these web-accessible resources by using a secret token to be required to access the web resource. However, z0ccc has released a method to bypass the secret token, called a ‘resource timing comparison’.
“Resources of protected extensions will take longer to fetch than resources of extensions that are not installed. By comparing the timing differences you can accurately determine if the protected extensions are installed,” explained z0ccc on the project’s GitHub page.
As a proof of concept, z0ccc released a Chrome Extension fingerprint site that will provide you with your installed Chrome extensions and how unique the combination is. The site/tool checks for 1,170 of the most popular extensions available on the Google Chrome Web Store.
A number of extensions that the site will discover include Honey, LastPass, uBlock, Adobe Acrobat, ColorZilla, Grammarly, and Rakuten.
The website will then generate a tracking hash based on the installed extensions which can be used to track that specific web browser, as shown in the image below.
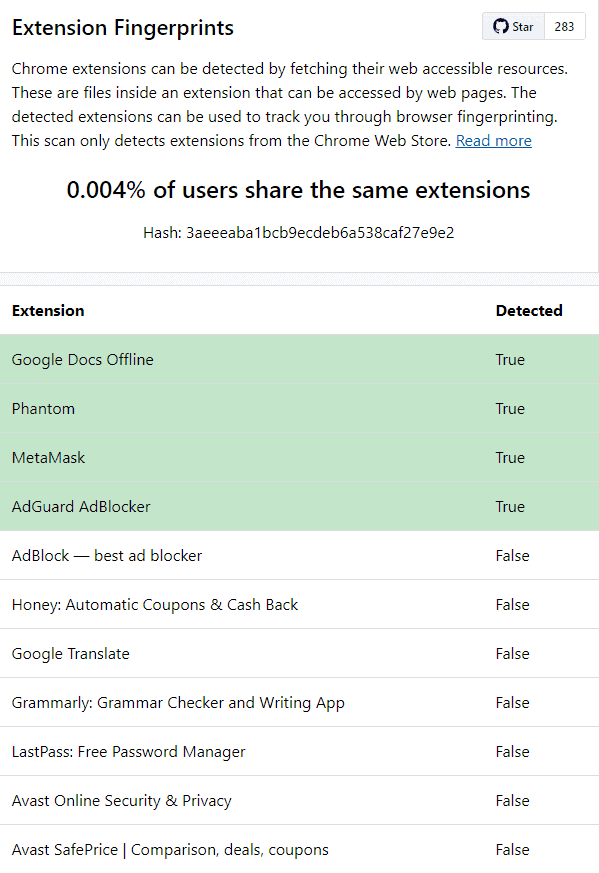
Some popular extensions such as MetaMask does not expose any extension resources, but z0ccc claims to still have identified the extension by checking if ‘typeof window.ethereum equals undefined.’ This method does not work with the Brave browser though.
Chrome browsers that contain no extensions will be less easy to fingerprint as they share the same fingerprint as all other Chrome browsers without extensions.
The Extension Fingerprinting site will only work with Chromium-based browsers with extensions installed from the Chrome Store. Even though this method can be used with Microsoft Edge, it will need to be altered to implement extension IDs from Microsoft’s store.
This strategy will not work with Mozilla Firefox add-ons as Firefox extension IDs are unique for each browser it’s installed on.
The most commonly installed extension
z0ccc is not collecting any data with his new project, but after doing his own tests, he has discovered that uBlock is the most commonly installed extension.
“By far the most popular is having no extensions installed. As previously said I do not collect specific extension data but in my own testing it seems that having only ublock installed is a common extension fingerprint,” z0ccc explained.
“Having 3+ detectable extensions installed seems to always make your fingerprint very unique.”
z0ccc stated that a 0.006% percentage indicates that you are the only user with that specific combination of extensions, but this may change as the site gets more hits.
The source of the new tool, Extension Fingerprints, has been released on GitHub using React which now allows anyone to start tracking users based on installed Chrome extensions.
bleepingcomputer.com/news/security/google-chrome-extensions-can-be-fingerprinted-to-track-you-online/
z0ccc.github.io/extension-fingerprints/







