Cado Security’s honeypot has recently captured a rather interesting cryptojacker from what they believe to be the WatchDog hacking group. They note that although the attack’s life cycle has many instances where TeamTNT’s payloads are used to execute various attacks, it is also very likely that it’s just a new campaign from WatchDog – a TeamTNT competitor – one previously known to use TeamTNT payloads to mount attacks.
They have referenced Palo Alto’s Unit42’s findings back in October 2021 which documented how a TeamTNT-transpired cryptojacking malware campaign was likely incorrectly attributed to TeamTNT and was a WatchDog campaign entirely.
Many characteristics that were found in that attack were also found in this attack, including:
- The usage of the oracle.zzhreceive[.]top domain
- The usage of the b2f628 directory naming in the URLs
- The usage of 43Xbg…-prefixed Monero wallet address
- The usage of the 1.0.4.tar.gz Compile on Delivery payload
- The avoidance of the usage of Golang payloads associated with Watchdog
Not everything is exactly the same which is to be expected as this is likely a new campaign, Cado Security notes.
The malware is designed to propagate like a worm and even includes a method to possibly compromise honeypots. Many scripts or payloads are quite similar and target Docker containers specifically.
WatchDog’s attack cycle
The Cado honeypot has documented the entire life cycle of the cryptojacking malware campaign by WatchDog. The initial access is made via the Docker Engine API and affected misconfigured endpoints within. Then, depending on whether or not the user is root, different scripts are loaded to process payloads.
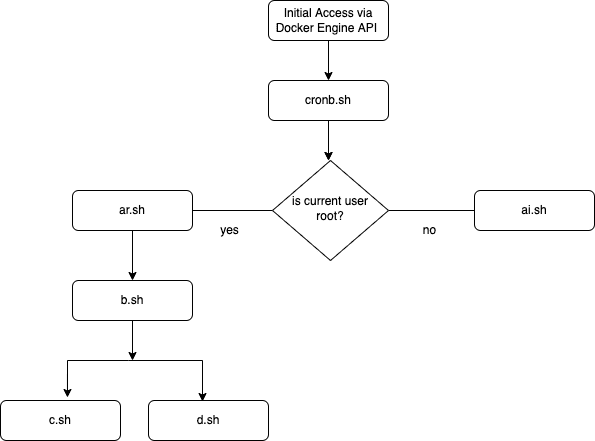
The attack is multi-stage and invokes many “interesting” functions including the clmo() function that hints, Cado believes, at a potentially repurposed code – from something that was aimed to target Linux servers and not specifically Docker containers.
This was, however, not the only instance of functions that hint at this. For example, the Alibaba Cloud Agent Removal process hints that the code was actually written to target Alibaba Cloud Linux servers and not Docker containers.
Throughout the attack cycle, a few of the many sophisticated techniques deployed by the malicious code include timestomping, exploitation of misconfigured Redis databases, and process hiding.
Cado’s report lists the indicators of a compromised system with filenames and their SHA256 hashes, URLs, and wallet IDs.
What are honeypots and how do they work?
Honeypots are used to detect, track, and analyze unauthorized access attempts against your network. Honeypots allow you to identify attacks that were unsuccessful due to the honeypot’s presence. They also provide valuable insight into the attacker’s motives and methods of attack.
A honeypot is a system, server, or device that is set up to mimic the key elements of an actual system in order to lure in attackers and study their behavior. The goal is to learn more about the attacker, who they are, and what they are doing. Honeypots can be used to track illicit activities, such as cyber threats, spam attacks, theft of personal data, and corporate espionage.
Honeypots are often used in tandem with other network security tools such as firewalls and intrusion detection systems (IDS). When deployed together, these tools can provide comprehensive security coverage for organizations large or small.
Honeypots work by luring attackers into thinking they have found an easy target for criminal activity. Once an attacker has been lured into attacking the “honeypot,” they can be monitored while they attempt to steal information or damage your network. The information gleaned from these attacks can help you understand how attackers work so you can better protect yourself against them in the future.







