An Advanced Persistent Threat (APT) hacking group based out of Iran going by the name Lycaeum has been seen using a .NET-based DNS backdoor to target organizations within the telecommunication and energy sectors Zscaler released in their report.
The APT group has been active since 2017 and has been known for targeting middle eastern organizations. But this group is now utilizing customized .NET-based malware, written in C#, which utilizes copied code from a popular open-source tool.
The code was ripped from DIG.net which is a tool made for carrying out DNS hijacking attacks, as well as executing commands, dropping payloads, and snooping on data.
Key attack features:
- The new malware is a .NET-based DNS Backdoor which is basically a customized version of the open-source tool “DIG.net”.
- The malware leverages a DNS attack technique known as “DNS Hijacking” in which an attacker-controlled DNS server manipulates the response of DNS queries and resolves them as per their malicious requirements.
- The malware employs the DNS protocol for command and control (C2) communication which increases stealth and keeps the malware communication probes under the radar to evade detection.
- The technique allows for Uploading/Downloading files and execution of system commands on the infected machine by abusing DNS records, including TXT records for incoming commands and A records for data exfiltration.
Basically, the threat actors are able to manipulate DNS queries to redirect users to a clone of a website under the assailant’s control. Any info entered on this cloned site such as usernames and passwords will then be shown to the attackers.
One Word doc
The attack begins, like many we see today, with a malicious Microsoft Word doc containing a macro downloaded from a fake news website “http[:]//news-spot.live”.

When the user enables the macro, the DNS backdoor is dropped to the user’s startup folder which is a technique utilized to start the malicious backdoor on every system startup.

A look at the new DNS Backdoor
The DNS backdoor is believed to be developed by the Lyceum Group. It has been widely used in their recent attack campaigns. As mentioned above, the backdoor is dropped and lives in the Startup folder of the infected system.
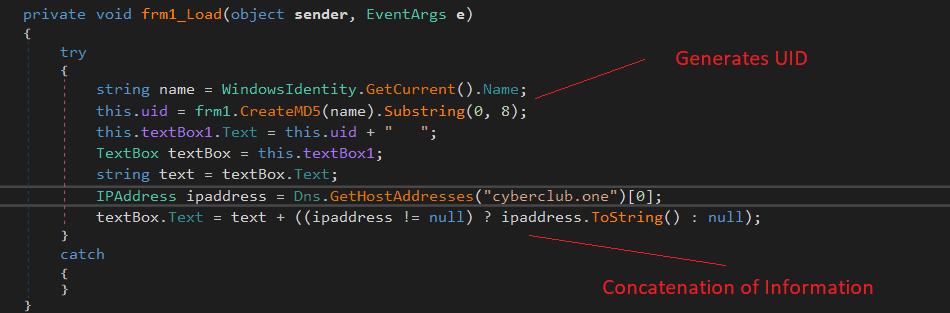
The backdoor’s executable name is set to “DnsSystem.exe” and the MD5 hash: 8199f14502e80581000bd5b3bda250ee.
“The threat actors have customized and appended code that allows them to perform DNS queries for various records onto the custom DNS Server, parse the response of the query to execute system commands remotely, and upload/download files from the Command & Control server by leveraging the DNS protocol.” – Zscaler
The malware begins the DNS hijacking process by grabbing the IP address from a DNS site “http://cyberclub[.]one” and then generates a unique victim ID based on an MD5 hash generated from the victim’s Windows username.

Who is the Lyceum APT group?
Lyceum is a team of hackers working on cyber espionage, and this new unique backdoor technique certainly is the mark of their progression in this field.
The Iranian hackers are anticipated to carry on engaging in these types of attack campaigns and are often involved with numerous threat groups from the country.
These APT threat actors are making a constant effort to evolve their tactics and strive to stay under the radar as long as possible. Despite how revolutionary this new backdoor technique is, there is still a need to enable macros within Word itself, which is an action that should rarely be taken.







