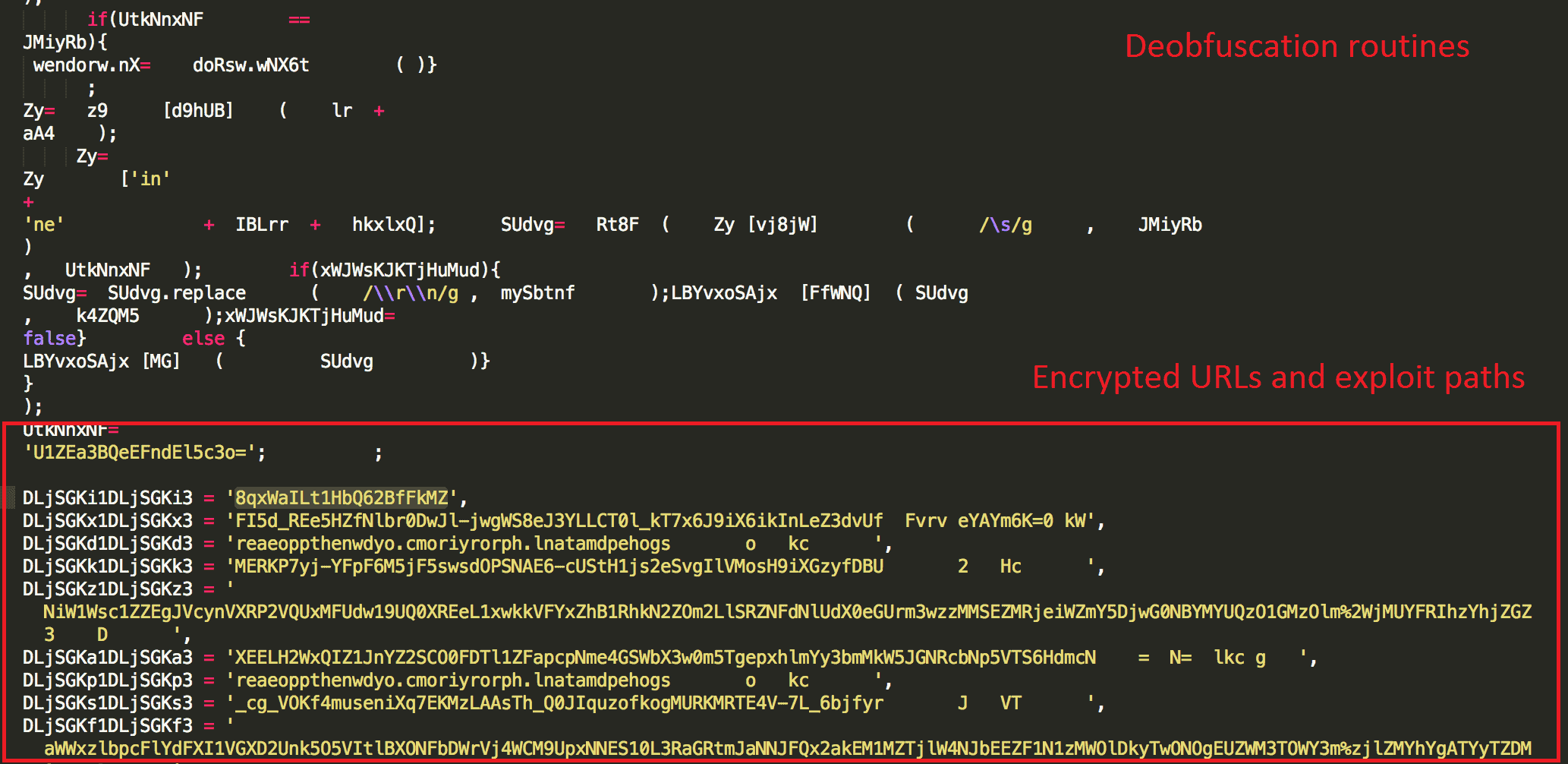
When a exploit has been discovered in an operating system or program the vendor pushes a patch or upgrade that eliminates the vulnerability. “Hardening” is the act of proactively protecting your server and minimizing damage if or when a zero-day attack impacts your server.
What you will need to focus on are the points listed below:
- Assume all installed applications are flawed—don’t rely on the security programmed into them.
- Physically remove from the system all applications not being used.
- Use firewalls, content filters and OS user authentication features to restrict access to the application, and provide access only to those who absolutely must have it.
- Update all applications to the latest patches when security bulletins are released.
- Internally developed applications need to be code-reviewed for security weaknesses. Consider an external security review for critical applications.
- Externally facing Web applications are high-risk applications because they are a bridge between the outside world and internal customer databases. Be sure to add code that can block or otherwise safely deal with all of the following hostile inputs: missing page parameters, parameters that are unusually long, parameters will nulls or hexadecimal encoding, parameters with Web browser script blocks (which are used to create server-side scripting attacks), and parameters with quotes and semicolons (likely attempts to send hostile SQL commands through to the database).
- If possible, write applications in languages that run in virtual machines–such as Java, Visual Basic .Net or C#–because they provide an extra layer of security protection. Avoid C and C++ because they make it easy to write applications that allow buffer overflow attacks.