Can Bluetooth signals be used to track smartphones? Many people would say “No” to this question. However, a team of engineers at the University of California San Diego thinks otherwise. Their latest report reveals that these engineers were able to demonstrate that Bluetooth signals are effective in identifying and tracking smartphones. Read further to learn more about the new Bluetooth signal discovery.
Bluetooth signals can track smartphones, a team of engineers reveals
If you’re familiar with mobile device technologies, you’re aware that they constantly transmit Bluetooth beacon signals. Yes, mobile devices, such as smartphones and fitness trackers often transmit these signals at an average rate of 500 beacons per minute. These signals make it possible for many features, including Apple Find My, to track lost devices easily.
In the past, many people have argued that Bluetooth signals aren’t effective in tracking mobile devices. However, the research by the UC San Diego engineering team reveals that Bluetooth beacons can accurately track smartphones and other mobile devices. The team presented the study on May 24, 2022, at the IEEE Security & Privacy conference in Oakland, California.
How do Bluetooth signals work for tracking smartphones?
The method of tracking mobile devices with WiFi fingerprints is pretty different from that of Bluetooth beacons. For WiFi, this fingerprinting method is based on a preamble or a long string, which is utilized to define a specific series of transmission criteria. On the other hand, the Bluetooth beacon tracking method is based on a shorter preamble.
According to one of the authors, Hadi Givehchian, the short preamble from Bluetooth beacon signals gives an inaccurate fingerprint. This explains why the tracking approach is not the same as the WiFi fingerprinting technique. Instead of using the same WiFi fingerprinting techniques, the researchers designed a new method, which doesn’t focus on using any preamble. Instead, the method uses Bluetooth signals for the tracking process.
For the tracking process to work, the researchers developed an algorithm that could estimate two different values in the Bluetooth signals. These values are carrier frequency offset (CFO) and I/Q in the Bluetooth Low Energy (BLE) signal. Furthermore, the researchers calculated the imperfections for each packet using the Mahalanobis distance, a measure of the distance between a point P and a distribution D, as Wikipedia defines.
Results of real-world experiments
Before arriving at the fact that Bluetooth beacon signals can accurately track smartphones and other mobile devices, the researchers carried out a series of experiments. In one of the experiments, the team of engineers found out that about 40% of the 162 mobile devices seen in public places were identifiable using the Bluetooth signal tracking method.
The researchers also experimented on over 647 mobile devices in a public hallway. This time around, they found out that 47% of the tested devices had unique fingerprints.
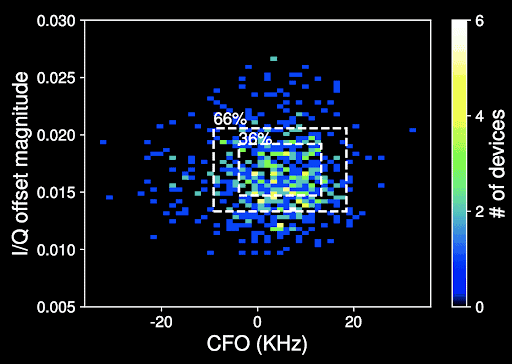
Furthermore, the researchers noted some factors that could affect Bluetooth beacon tracking. These factors include changes in ambient temperature and power ratio for various devices. Even though attackers can face these challenges, they will still have the ability to track many devices with this new Bluetooth tracking technique. The researchers also noted that the tracking process wouldn’t require using any sophisticated equipment.
Currently, the research team is working on a new way to conceal the Bluetooth fingerprints in the Bluetooth device firmware through digital signal processing. They are also looking for a way to apply the newly developed method to other devices. Here’s a brief of what Prof. Dinesh Bharadia of UC San Diego’s Department of Electrical and Computer Engineering said regarding the experiment:
“Every form of communication today is wireless and at risk. We are working to build hardware-level defenses to prevent potential attacks.”







