Today Kaspersky Lab’s security investigation group released the discovery of “The Mask” (aka Careto) via a blog post today. “The Mask” is a sophisticated Spanish-language threat that’s been associated with global cyber-espionage operations since around 2007. The thing that makes The Mask unique is the sophistication of the toolset utilized by the attackers. Including an incredibly sophisticated malware, a rootkit, a bootkit, Mac OS X and Linux versions and perhaps versions for Android and iOS devices.
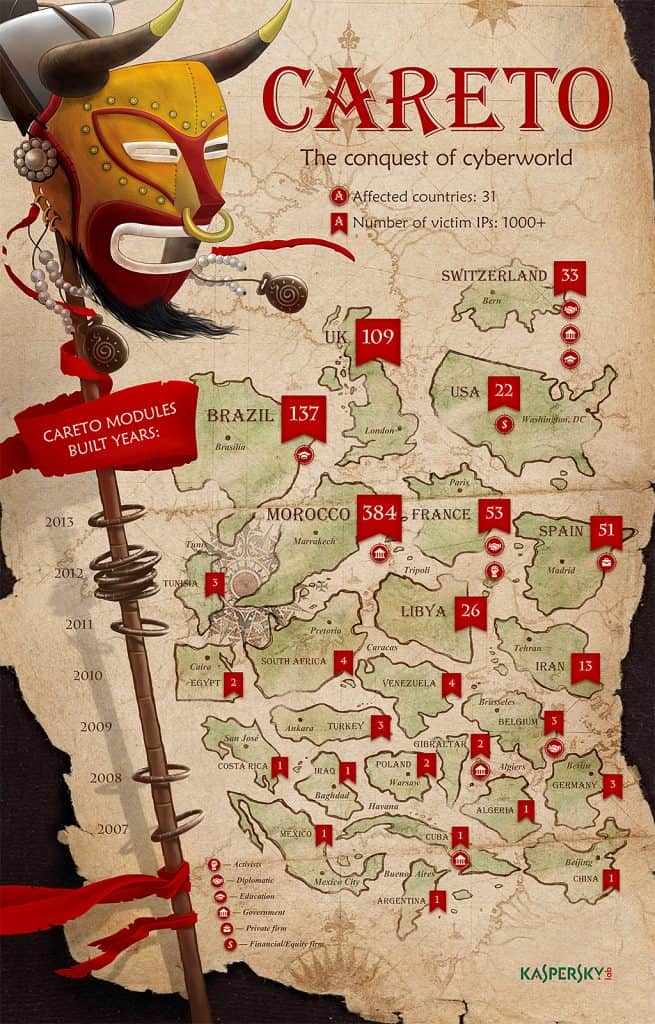
The main targets as you might have guessed are “government institutions, diplomatic offices and embassies, energy, oil and gas companies, research organizations and activists. Victims of this targeted attack have been found in 31 countries around the world – from the Middle East and Europe to Africa and the Americas.”
The malware gathers as much data as it can collect, this includes office documents, but will also swipe a variety of encryption keys, VPN configurations, SSH keys and RDP files. All basically allowing the attackers to access any servers that are associated with the infected device.
“Several reasons make us believe this could be a nation-state sponsored campaign. First of all, we observed a very high degree of professionalism in the operational procedures of the group behind this attack. From infrastructure management, shutdown of the operation, avoiding curious eyes through access rules and using wiping instead of deletion of log files. These combine to put this APT ahead of Duqu in terms of sophistication, making it one of the most advanced threats at the moment,” said Costin Raiu, Director of the Global Research and Analysis Team (GReAT) at Kaspersky Lab.
“This level of operational security is not normal for cyber-criminal groups.”
You can view the full write up and analysis by Kaspersky here.
Kaspersky Lab experts originally had this new thread brought to their attention a year ago after they noticed efforts to exploit a vulnerability within the company’s products that was patched five years earlier. The exploit offered the malware the power to prevent detection. Obviously, this situation elevated their curiosity which is how the investigation began.
Careto intercepts all types of communications and collects only the vital details from the victim’s device. Detection is incredibly challenging due to the stealth rootkit functions.
You can view the FAQ list on Kaspersky’s blog located here.
Based on Kaspersky Lab’s investigation statement, The Mask campaign relies upon spear-phishing e-mails with hyperlinks to a malicious site. The malicious website includes a variety of exploits modified to infect the visitor, based on system configuration. Once infected, the site will redirect an individual to said website referenced within the e-mail, which may be a YouTube video or even a news article, leaving the end-user completely blind to what really occurred.
Main Findings (Credits to Kaspersky.com)
Main findings:
- The authors appear to be native in the Spanish language which has been observed very rarely in APT attacks.
- The campaign was active for at least five years until January 2014 (some Careto samples were compiled in 2007). During the course of Kaspersky Lab’s investigations, the command-and-control (C&C) servers were shut down.
- We counted over 380 unique victims between 1000+ IPs. Infections have been observed in: Algeria, Argentina, Belgium, Bolivia, Brazil, China, Colombia, Costa Rica, Cuba, Egypt, France, Germany, Gibraltar, Guatemala, Iran, Iraq, Libya, Malaysia, Mexico, Morocco, Norway, Pakistan, Poland, South Africa, Spain, Switzerland, Tunisia, Turkey, United Kingdom, United States and Venezuela.
- The complexity and universality of the toolset used by the attackers makes this cyber-espionage operation very special. This includes leveraging high-end exploits, an extremely sophisticated piece of malware, a rootkit, a bootkit, Mac OS X and Linux versions and possibly versions for Android and iPad/iPhone (iOS). The Mask also used a customized attack against Kaspersky Lab’s products.
- Among the attack’s vectors, at least one Adobe Flash Player exploit (CVE-2012-0773) was used. It was designed for Flash Player versions prior to 10.3 and 11.2. This exploit was originally discovered by VUPEN and was used in 2012 to escape the Google Chrome sandbox to win the CanSecWest Pwn2Own contest.