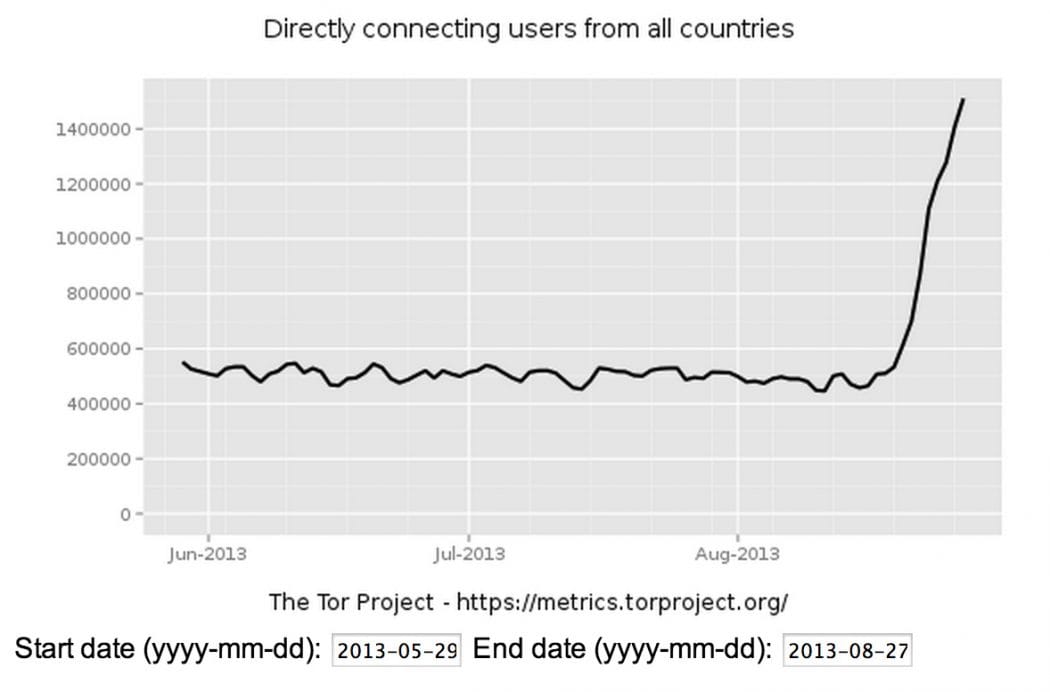
The Tor network has been getting a lot of attention lately. About two weeks ago, the number of users on the anonymous network mysteriously doubled, hitting a record high.
It could be because of the new Pirate Bay’s new Tor-powered browser. It could also be a result of recent web censorship by the Russian government. Or it could be new malware that is utilizing the network to hide their Command and Control (C&C) servers.
A new report from the US Naval Research Laboratory and Georgetown University in Washington DC called “Users Get Routed: Traffic Correlation on Tor by Realistic Adversaries.”
Researchers claim that It is not very difficult to expose the bulk of user’s identities if an attacker is willing to put in the time and effort, according to the Register. It’s even easier for government and spy agencies that have money to do so.
So, how bad is the security risk? The study found that even if an attacker had no control routers, 80 percent of Tor users could be de-anonymized within six months. With control of one exchange point, or autonomous systems (AS), around 100 percent of users were likely to be uncovered, within three months. With two, it could take just one day.
“These results are somewhat gloomy for the current security of the Tor network,” researchers wrote, adding that “Current users of Tor should carefully consider if it meets their security needs.”