We’ve been contacted by HD_Breaker, a pen-tester and co-manager of Underc0de.org, with information on a security flaw in Kim Dotcom’s newly launched site, Mega.co.nz.
HD_Breacker also provided a point of concept (POC) for this bug.
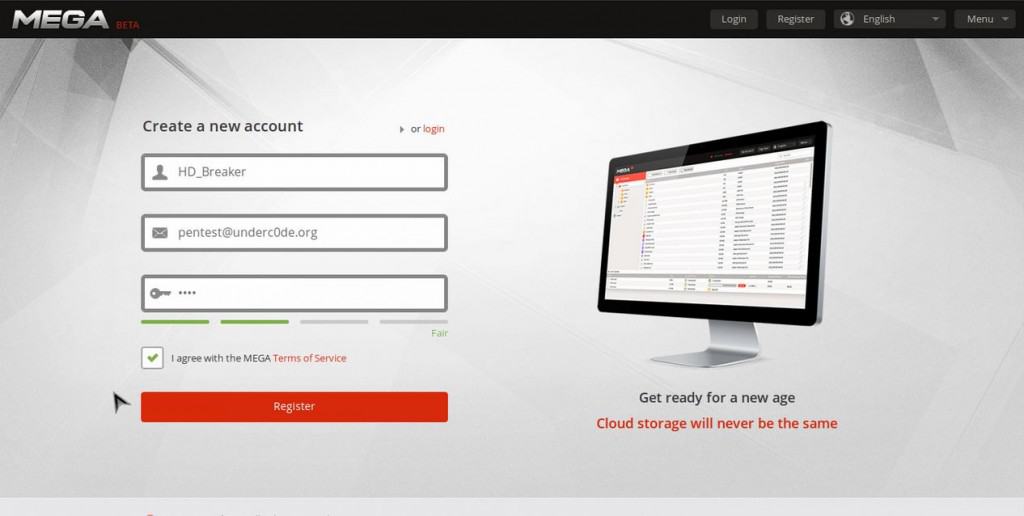
To carry out this exploit, you need to go to the registration page of Mega’s site, put in false info, and click register.
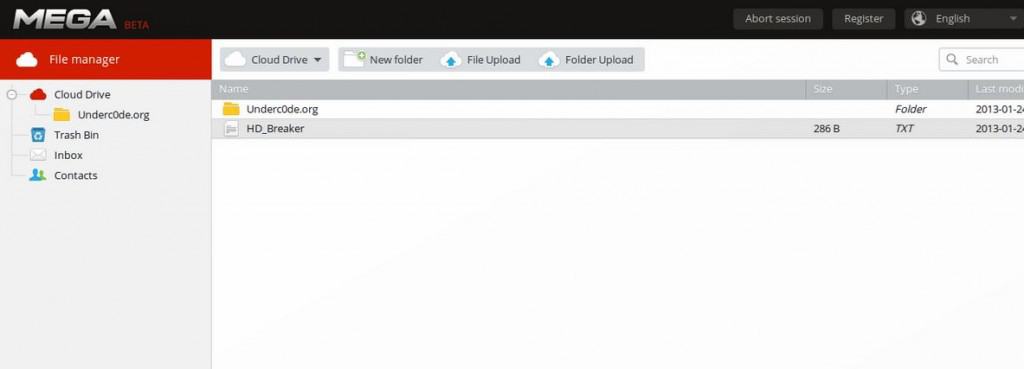
Then, you will be on a page that states registration successful and you will see a button in the top right corner stating “Abort Session”. Now, press the back button on your web browser and you should be in a cloud drive.
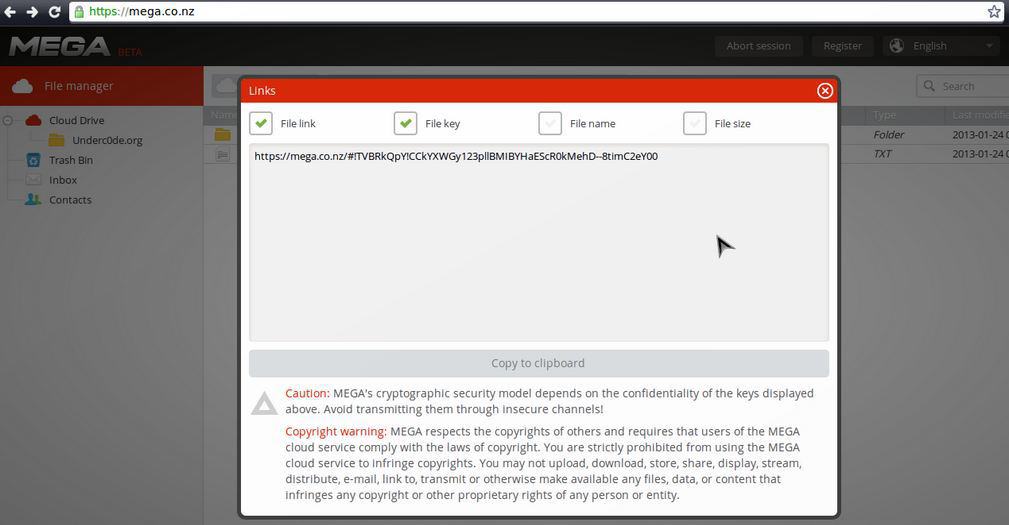
With this bug you can also generate your own encrypted links, and have all the abilities without an account.







“MEGA supports ephemeral accounts to enable pre-registration file manager
operations, allowing applications to present MEGA’s functionality with a
lowered barrier to entry. They naturally do not have an e-mail address
associated with them, the password (master key) is generated randomly,
and they are subject to frequent purging. In a browser context, the
credentials for ephemeral accounts live in the DOM storage.”
This is from their API part of their website, this ain’t a “bug”. It is actually left that way on purpose, you can read more on https://mega.co.nz/#developers , section 1.5 User/session management