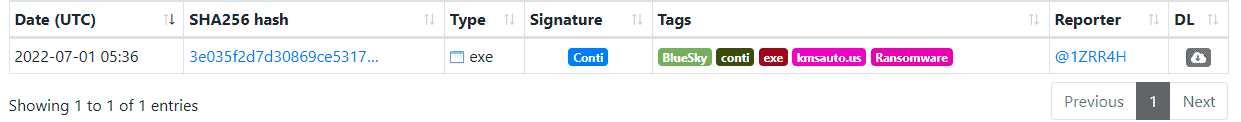
A financially motivated threat actor has been discovered spreading a new ransomware strain, dubbed BlueSky. The group is believed to be connected to the Conti ransomware group.
CloudSEK’s AI digital risk platform XVigil has discovered the new threat and found that the ransomware is currently targeting organizations and demanding ransom in the form of Bitcoin (BTC).
Bluesky Ransomware breakdown
Bluesky has been seen encrypting the victim’s files with a ‘.bluesky’ extension and then dropping a ransom note via a TXT file.
The researchers have discovered that the ransom is required to be paid in BTC, and have also identified multiple BTC addresses being generated, leading them to believe each victim receives a unique BTC address.
“A Twitter post indicates that one of the BTC addresses has transacted around 1.59 BTC while the other one has no recorded transactions so far,” Cloudsek Added in their report.
Information & analysis – KMSAuto infected
- BlueSky ransomware was discovered in the wild with a filename of ‘javaw.exe’ and was 71KB.
- ‘javaw.exe’ was dropped by a PowerShell script named ‘2.ps1‘ which was 16.84KB.
- After further investigation, the researchers discovered that 2.ps1 opened communications with a domain pretending to be an old Windows activation too called “KMSAuto Net Activator“.
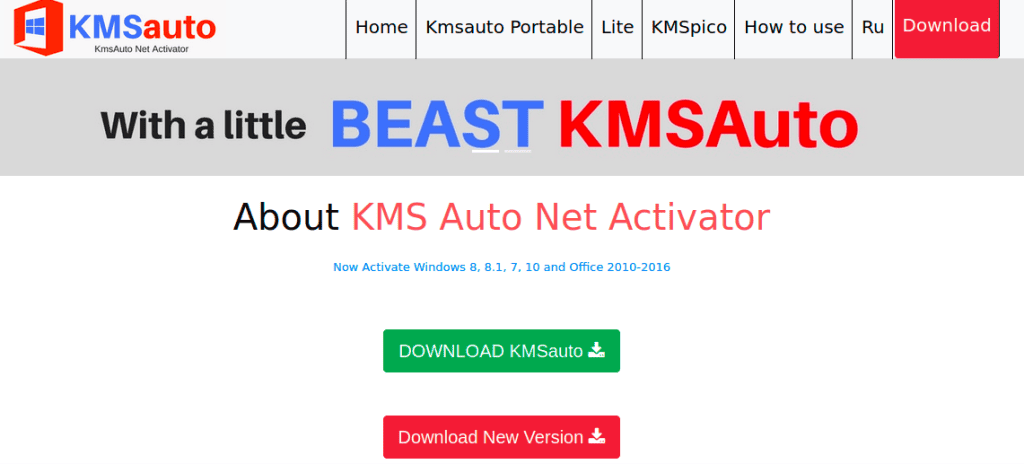
The malicious PowerShell file contacts a server run by the threat actors with the domain kmsauto.us and downloads a file hxxp://kmsauto.us/someone/l.exe.
The “someone” directory in the web address contains multiple executables including the BlueSky Ransomware. The other executables include:
- JuicyPotato
- CVE-2022-21882
- CVE-2020-0796 aka SMBGhost
Ransomware operator
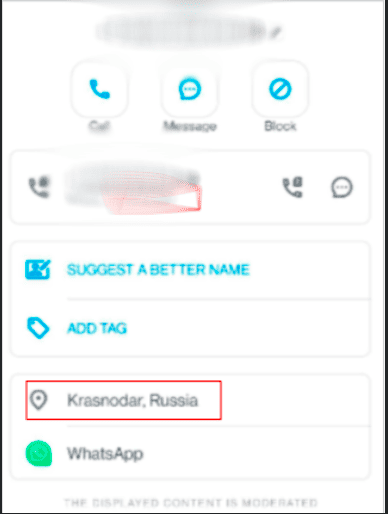
After the researchers discovered the new ransomware strain, they pulled the Whois and DNS records providing them with a registration email and phone number associated with the domain name.
The researchers then discovered the phone number was associated with the Krasnodar region in Russia and has an active WhatsApp account.
Researching the domain’s activity revealed that the last edit was done in 2021, only a year after the domain was registered.
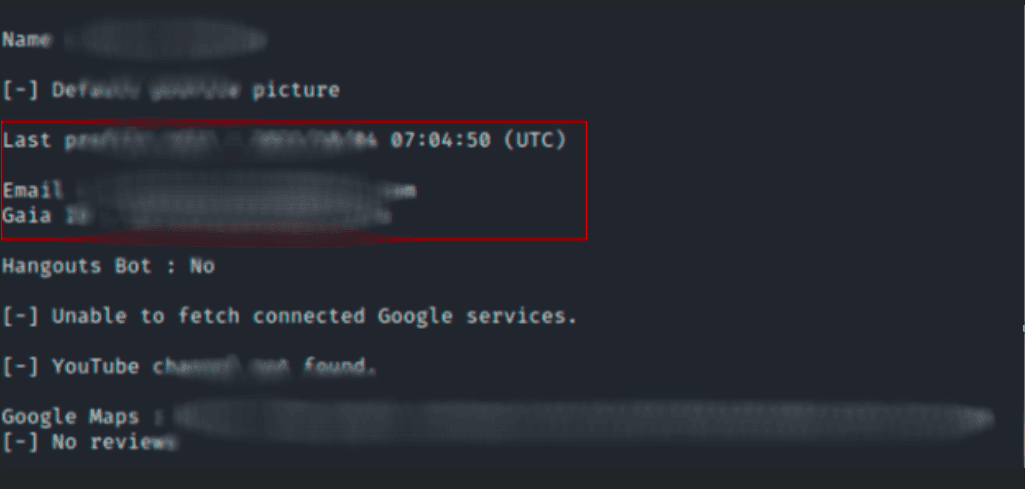
The website operator most likely originates from Russia due to these findings:
- They have social media mentions on VK which is the largest Russian line media and social networking service.
- The following pages on the website contain Russian words which loosely translate to criminal, religion, and economy.
- https[:]//kmsauto[.]us/v-mire/
- https[:]//kmsauto[.]us/kriminal/
- https[:]//kmsauto[.]us/religiya/
- https[:]//kmsauto[.]us/ekonomika/
Linked in Conti Ransomware?
Cloudsek suspects that BlueSky has some connection with the Conti ransomware due to the malware being tagged along with Conti on file analysis and sample sharing sites. The two groups share common file signatures as well.