The Marcher Banking Trojan, which is sold on underground Russian forums for around $5,000, is an Android banking Trojan that’s been available since late 2013. The malware was first made to display phishing webpages on top of Google Play to fool users into passing over their bank card information.
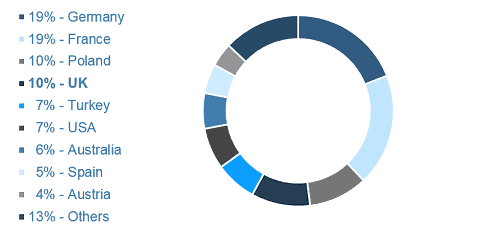
Although, in March 2014, a new variation of the malware had been identified targeting banks in Germany. The list of targeted nations was eventually broadened to incorporate France, Poland, Turkey, the United States, Australia, Spain, Austria, and many others.
IBM Security experts happen to be tracking the mobile banking Trojan and found that, in late May, its writers included nine leading banks in the U.K. to the roster of targets.
Aggregating Marcher configurations permits us to see its top desired geographies.
Marcher targeting countries listed below:
The Trojan has been overlaying screens to acquire details from victims. Many times, the overlay screens are personalized for the targeted bank and are hardcoded or fetched from a server by the malware.
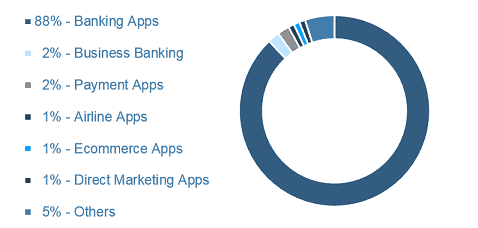
Even though the Trojan has mainly targeted mobile banking apps, it also has the ability to steal info from payment, airline, e-commerce, and direct marketing apps.
Current list of applications the Trojan is targeting:
As opposed to other Android banking malware, Marcher doesn’t only focus on apps. The phishing screens are visible both on top of financial apps and the bank’s website when individuals access it in an internet browser. Analysts found overlay displays being shown over Austrian and Australian financial websites.
Marcher also has the ability to intercept SMS messages and phone calls, which can be ideal for a few things. First, it permits attackers to forward messages and phone calls that contain info sent to the user by the bank’s two-factor verification system. Additionally, by getting control of SMS and mobile call applications, criminals could make calls and send messages to premium-rate numbers to create an extra money source.
To stop yourself from being a victim, you can install any popular Android antivirus app.







