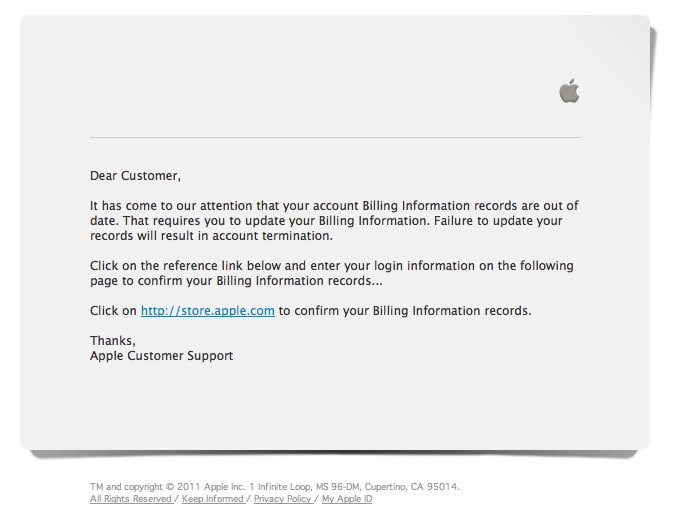
Based on the 2014 Global Phishing Study, Apple has become the “world’s most-phished brand.” A phishing attack is one in which a hacker sends you a text or email appears to be from a legitimate business or friend, and attempts to trick you into entering private data, a credit card number or any other financial details.
The Global Phishing Survey notes there have been “at least 123,741 unique phishing attacks worldwide” within the first half of 2014 that each targeted a unique brand or entity. Almost 23,000 domains “were registered maliciously by phishers,” mostly in China, the report mentioned.
Phishing attacks are typical on all systems, not just Apple products. The attacks don’t rely upon technology, but on psychology (Social engineering): they attempt to fool users into giving up private info by impersonating websites or people they trust.
Even so, if you know what to look for, it’s often simple to differentiate between a legitimate email and a phishing attack.
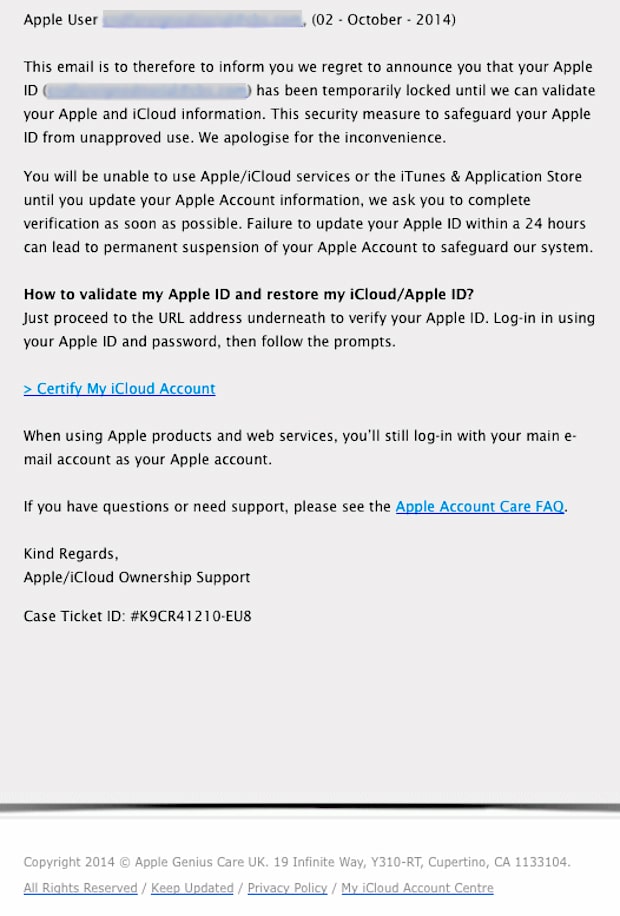
iCloud and Apple phishing email:
Satnam Narang, Security Response Director for Symantec, explained the indicators in this particular phishing email. “The subject is weird. ‘Apple Service Locked’? Apple wouldn’t write something like that,”. Another giveaway? “The ‘to’ line is addressed to a generic name, ‘Apple user,’ and an email address. Apple knows your Apple ID.”
And read carefully: “It is written in broken English,” Narang observes. The address on the bottom says ‘Apple Genius UK,’ then gives an address in Cupertino, CA.
You must also be aware of other personal information, like the answer to your security question, which could be used to hack into Apple or other accounts.