Cryptolocker is now being spread around YouTube by vxers who’ve purchased advertising space, researchers Vadim Kotov and Rahul Kashyap have discovered.
The researchers made the discovery while checking YouTube and website banners for situations where malware writers had in fact bought space to spread their malware on unpatched users.
The researchers who will present at the upcoming Virus Bulletin 2014 conference in Seattle wrote in a paper advertisement networks was a viable way to flog virus and trojans.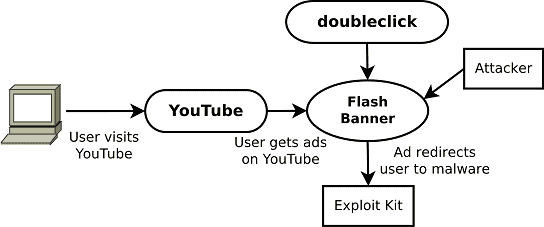
The researchers who’ll present at the approaching Virus Bulletin 2014 convention in Seattle wrote in a paper advertisement networks was a feasible method to spread virus and trojans.
“We conclude that ad networks could be leveraged to aid, or even be substituted for current exploit kits,” they said.
Ad space was a cheap and efficient way to spread browser malware enabling attackers to filter victims by language, location, and interests, VB documented. Malware found in ads might be obfuscated and then unleashed once conditions like operating systems, browser versions along with other factors were met.
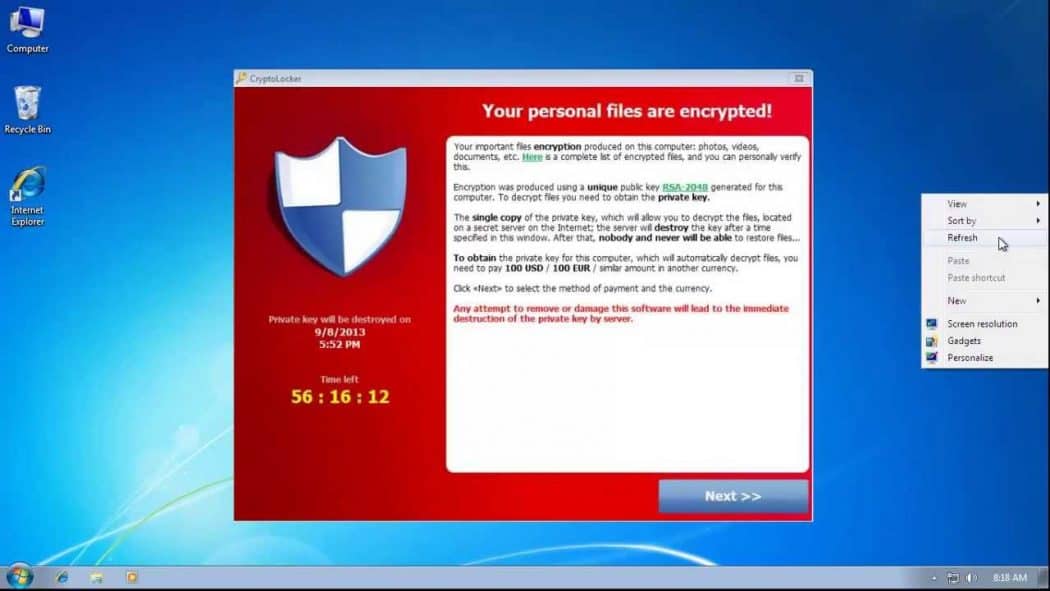
The CryptoLocker appeared in September spread via Gameover ZeuS. It encoded important files including images and documents on affected Windows machines prior to requiring that victim pay up to $500 in BitCoins within 72 hours for the private keys required to unlock files.
CryptoLocker utilized AES symmetric cryptography to encrypt the files and encrypted the AES key using an RSA-2048 bit public key generated on its server side.
The researchers stated there was very little advertising networks could do to prevent the attacks.