The Microsoft Malware Protection Center (MMPC) is warning corporations in regards to a new malware strain dubbed TrojanSpy:Win32/Gamker.A which is targeting SAP software
SAP with it’s headquarter located in Germany produces business software apps to track and control business operations. Gamker looks to be the very first ever-malware strain developed by crooks targeting SAP but may not be the last.
Part of Gamker code resembles Carberp’s code, the financial stealing bot, source code which was revealed earlier this year, along with the ‘remote control code’.
McDonald said that the bot contains a VNC (virtual network computing) so Gamker possess the ability to control a infected machine remotely. The attacker can initiate a VNC session to get any other particulars to hijack the SAP server and can also hit the SAP server from the contaminated machine.
Gamker contains a keylogging feature which records all ‘keystrokes’ entered into any app operating on a tarnished computer and this aspect has the potential to take all login details like ‘usernames’ and ‘passwords’ that offers those entered in SAP patron apps.
The malware has a thorough list of specific programs for that it also preserves command line parameters and captures screenshots of their task windows.
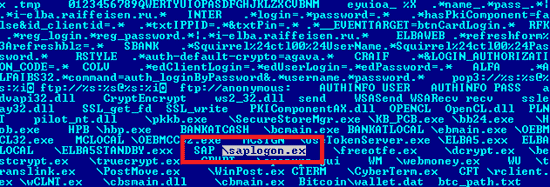
McDonald included that this is a specific attack on SAP itself and not merely a innocent information gathering process to establish the installation of SAP. The crooks are using execution of SAP component ‘saplogon.exe’ to initialize footage of the disagreements of command line passed into it together with ten screenshots to the ‘C7C server’.
MMPC declares that the fact that this Trojan is striking businesses instead of individual home-users is suprising.
MMPC urged in its concluding declaration that to minimize the harm on their ‘SAP’ machines by possible attacks, firms must give users the minimum access privilege levels vital to accomplish their works, must use 2FA (two-factor authentication), scan their systems with anti-malware programs, and educate the users.