 Microsoft has discovered that a lot of the code applied by the Nitol malware family is copied from free malware. Microsoft posted portions of the code online this week where similar lines used for denial of service attack functionality are present in Nitol and on the sites in question.
Microsoft has discovered that a lot of the code applied by the Nitol malware family is copied from free malware. Microsoft posted portions of the code online this week where similar lines used for denial of service attack functionality are present in Nitol and on the sites in question.
The Nitol botnet was recently taken down by Microsoft after it was given permission by the U.S. District Court for the Eastern District of Virginia to take charge of the 70,000 sub domains hosting malware on the 3322.org domain.
Microsoft has been looking into supply chain protection for some time—its recent Security Intelligence Report concentrated on malware compromising third-party suppliers, P2P networks and sites—and accounted in September that it had exposed Nitol malware pre-loaded on computers built in China running fake versions of the Windows operating system.
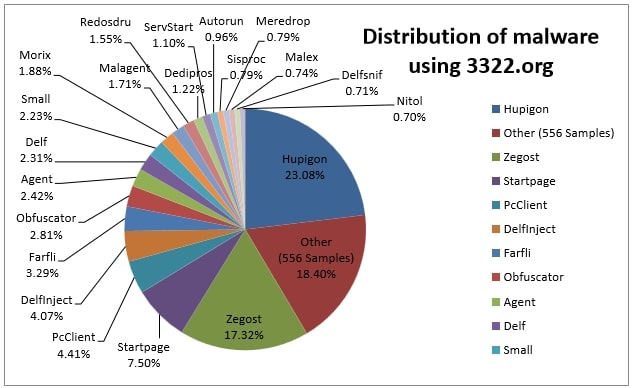
The 3322.org subdomains, meanwhile, were hosting more than 500 strains of malware, including DDoS malware, keyloggers, rootkits and more.
The compromised machines then issued commands to attack domains by a assortment of means, including SYN, UDP, TCP, HTTP and ICMP floods. The C&C server can also send additional executables or updates to infected machines, or force a browser to surf to a compromised URL.