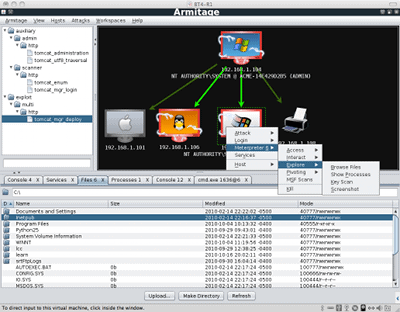
Basically, Armitage is a program written in java, it provides a gui to the Metasploit framework.
Armitage will not work if your Metasploit installation pre-dates Metasploit 4.0. You may type msfupdate a thousand times and this fact will not change. If you have an old Metasploit installation, you must uninstall it and install Metasploit with the latest installer to use Armitage.
Armitage can be used on both Windows and Mac OS platforms.
You can download from our site, or the official Armitage website.