Shylock, a new banking variant, has been discovered which includes the capability to spread over Skype.
Shylock was first detected in 2011 by researchers from Trustee firm, which also was used to take banking credentials from its victims. The first edition of the malware presented improved methodology for injecting code into browser to control the victim and an improved evasion method to prevent detection by usual antivirus software.
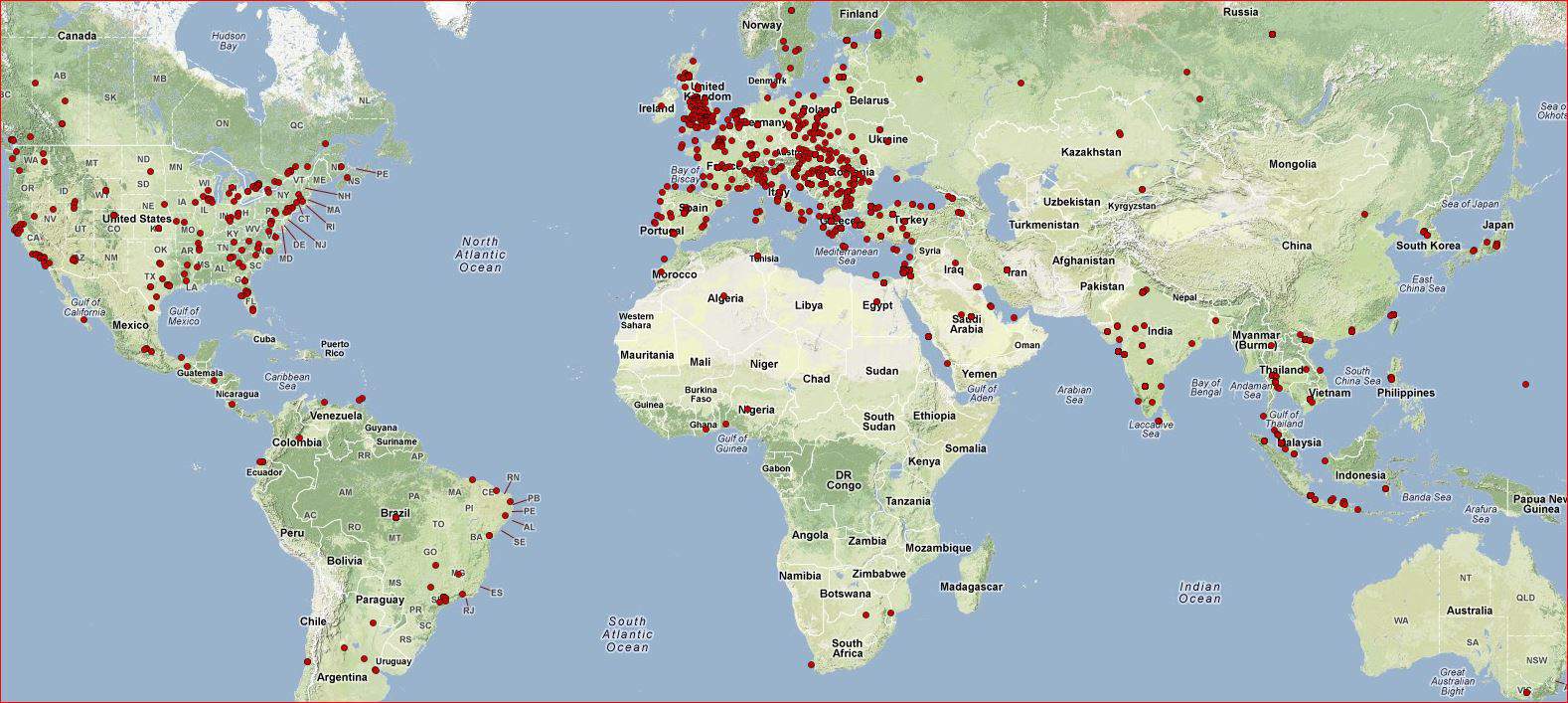
Shylock moves in only a few parts of the world. The epicenter of infections is mainly located in the UK. If we consider the sinkhole data collected by CSIS it turns out clear that the attackers choose to focus merely on a few countries rather than random infections in different countries.
The authors of malware have developed a plugin named “msg.gsm” that allows for the code to spread through the popular VOIP client including the following functionality:
- Sending messages and transferring files
- Clean messages and transfers from Skype history (using sql-lite access to Skype%smain.db )
- Bypass Skype warning/restriction for connecting to Skype (using “findwindow” and “postmessage”)
- Sends request to server: https://a[removed]s.su/tool/skype.php?action=…